Smart homes are beautiful. Lights that adjust automatically, thermostats that anticipate your presence, cameras that offer peace of mind, and vacuum cleaners that quietly crawl across the floor, building a detailed 3D map of your home. Yet this very intelligence, without transparency, can transform a private space into a sensor-driven environment. Every movement, every sound, every pattern of activity, even the placement of your furniture and desk, becomes data. Where does that data go, how is it stored or analyzed, and who ultimately controls it?
Before we can call a home “smart,” three questions must be clearly answered:
- Ownership of hardware and software: Do you truly own the device, or are you merely renting permission to use it?
- Data sovereignty: Where is the data sent, and under the jurisdiction of which country’s laws does it fall?
- Remote control channels: Who can issue commands, perform updates, or even disable your device from afar?
Field experience shows that in many IoT products originating from China, the practical answers to these questions tend to work against the consumer.
Case One: My Vacuum Turned Against Me
One of the most well-documented examples is the story of a software engineer who tried to limit the telemetry sent by his robotic vacuum cleaner (iLife A11) to Chinese servers. He set up a simple rule in his firewall to block “high-volume logging” but left the update channels untouched. For a few days, everything worked fine. Then the device suddenly died. It was taken to a service center, returned “fixed,” and a few days later, died again. Once the warranty expired, the engineer decided to find out why, armed only with a screwdriver and his technical know-how.
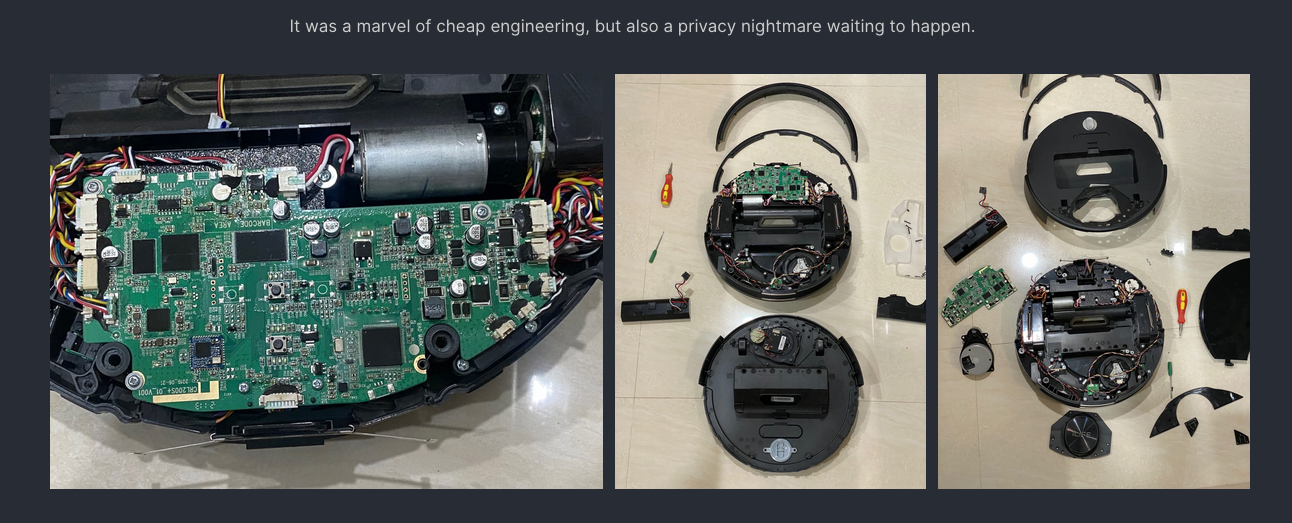
A software and hardware teardown revealed that this vacuum cleaner was essentially a fully functional Linux computer. It had an open ADB port with no authentication (allowing anyone on the same network to access it), stored the user’s Wi-Fi credentials in plain text, and used Google Cartographer to build precise indoor maps. But the smoking gun was elsewhere: the logs showed that at the exact moment the device went offline, someone had remotely connected and deliberately altered the startup script of the main application, effectively triggering a “kill switch.” The mechanism of remote access also became clear: a package called rtty with root privileges, allowing the manufacturer to execute commands, transfer files, and modify scripts on the device. The likely outcome? Once telemetry was blocked, the vacuum became “offline and inoperative” at home, but when brought into the service center’s open network, it reconnected to its master server, received a recovery command, and worked for a few more days until it was again placed behind the user’s firewall and failed once more.
Two crucial insights emerge from this case. First, this is not merely a “security flaw” but an instance of actual remote control. Second, it is not confined to a single brand. The CRL-200S hardware platform and its associated software infrastructure (attributed to 3irobotix) have been identified in a range of robotic vacuums sold under different brand names, from Xiaomi to Proscenic and Viomi. In other words, the backdoor is a platform-level issue, not an isolated bug. This means millions of households may unknowingly host a device that maps their home in 3D, has access to microphones and cameras, and can serve as a potential pivot point for compromising other sensitive devices on the same home network, such as laptops or smartphones.
Case Two: When a Car Becomes a Moving Microphone
If a robotic vacuum can be shut down remotely, imagine the surveillance potential of a fully connected electric car. The short answer is “much greater”. Modern vehicles are essentially computers on wheels, equipped with multiple ECUs, constant network connectivity through embedded SIM cards or Wi-Fi, numerous sensors, cameras, microphones, high-precision GPS, and continuous over-the-air updates. When the data sovereignty and supply chain of both hardware and software fall under China’s jurisdiction, the national security risks multiply significantly.

This scenario recently led to a decisive move in Israel. Based on intelligence assessments, the Israel Defense Forces (IDF) began collecting Chinese-made vehicles from officers and is gradually replacing its fleet with non-Chinese brands. The short-term goal is to eliminate the risks posed by cameras, microphones, and opaque connectivity near classified facilities. The long-term goal is to end operational dependence on platforms that could enable covert surveillance, movement tracking, or even environmental audio monitoring.
Israel is not alone. Both the United Kingdom and the United States have also introduced restrictions on the presence of Chinese-made vehicles in sensitive security zones. Likewise, China itself has imposed limits on Tesla vehicles operating near critical infrastructure. The shared logic is clear: highly detailed motion profiles and environmental audio-visual data, when stored or analyzed outside a nation’s own jurisdiction, can rapidly transform from raw data into actionable intelligence.
Case Three: Iranian Appliances with Chinese Roots
RaazNet’s previous report into the Snowa–Daewoo supply chain in Iran offers a concrete example of this “blended” risk at the consumer level. Televisions, air conditioners, refrigerators, and smart vacuums may appear to be ordinary household products, yet beneath their surfaces they rely on Chinese manufacturing chains and foreign cloud-based software platforms.
Raaznet previous report: Homes That Switch Off
The central concern is this: what kinds of data do these companion apps, cloud servers, analytical SDKs, and preinstalled modules actually collect from inside a home? How are microphone, camera, and network permissions managed? And ultimately, where exactly do these data sets go, and under what legal frameworks are they stored? In the absence of contractual transparency, third-party audits, and enforceable accountability, the apparent affordability and accessibility of such devices come with an invisible cost of surveillance. What seems trivial today could tomorrow endanger the professional security of a journalist, a civil activist, or an employee working in a sensitive institution.
Why This Is Systematic, Not Accidental
Three technical and economic pillars make this pattern of surveillance systemic rather than coincidental.
- OEM and ODM platforms: Major component manufacturers and reference platform providers, from chipsets to SDKs and cloud frameworks, sell “all-in-one” solutions to dozens of brands. If a backdoor exists at the platform level, it spreads horizontally across brands, as seen in the 3irobotix case.
- Telemetry economics and machine learning: Large-scale data collection is necessary for product optimization, but the line between optimization and profiling is extremely thin, especially when the data is sent to jurisdictions with weak transparency and accountability.
- State-industry alignment in China: In China’s governance model, technology and data companies are legally and structurally obliged to cooperate with state security entities, whether directly or indirectly. Even a company’s good intentions cannot exempt it from the weight of government mandates.
Verification Standards: From Claims to Evidence
To move beyond general warnings, each claim must be tested against verifiable evidence.
- A real, not hypothetical, kill switch: Device logs, the altered startup script at the moment of shutdown, and the presence of the rtty tool with root access are clear technical indicators. These show that the incident was not a random bug or local misconfiguration but a case of actual remote control.
- Platform-level exposure, not brand-specific: The exclusive linkage of the companion app to 3irobotix servers and the shared hardware platform across several brands extend the risk horizontally across the market.
- A costly institutional decision (IDF): For the Israel Defense Forces to recall and replace Chinese-made vehicles amid war and budget constraints suggests a genuine security signal, not a theoretical risk. Even if evidence of direct compromise has not been made public, the weight of such assessments should not be underestimated.
Policy Response: Transparency, Audits, and Rational Localization
For policymakers, procurement officers, and professional consumers, several actionable steps can mitigate these risks.
- Data-level contractual transparency: User agreements and product terms must explicitly define the type of data collected, where it is sent, how long it is stored, and who the third-party recipients are. Anything less represents a significant risk.
- Pre-deployment audits: Every IoT device deployed in a sensitive environment must undergo code, traffic, and framework auditing, from identifying open debug services such as ADB to detecting remote tunneling services like rtty or Dropbear.
- Secure network architecture: Isolate IoT Wi-Fi networks from work or personal networks. Restrict outbound traffic to a whitelist of approved domains and IPs, and review traffic logs regularly. The golden rule: assume the device is compromised and design your network so the damage stops there.
- Procurement hygiene: Cameras, vehicles, household appliances, and sensors used in media or government facilities should come from a vetted “secure supply list.” They should include enforceable requirements for hardware-level microphone and camera disablement in specific models, as well as the option for software-based air-gapping.
- User right to real offline mode: Every device should have a full local mode. If a user disables telemetry, the device must continue functioning. This should be a consumer protection standard, not a manufacturer’s courtesy.
- Data storage under secure jurisdiction: Consumer data must be hosted in jurisdictions with strong privacy and accountability standards, subject to independent audit and legal recourse.
Practical Recommendations for Your Home and Car
- Separate all IoT devices on a dedicated Wi-Fi: Use a secondary router or a properly isolated VLAN for your TV, vacuum cleaner, cameras, smart bulbs, and speakers. Simply using separate SSIDs does not ensure isolation, as most consumer routers do not fully segregate traffic between networks.
- Limit network output: If your router allows it, implement egress filtering based on a whitelist so that each device communicates only with approved domains.
- Less is better: Disable unused features such as always-on microphones, voice control, and ambient cameras, preferably through hardware switches or physical covers.
- Update, but monitor: Keep your devices up to date, but observe traffic patterns. If data behavior changes significantly after an update, investigate further.
- Treat your home map as sensitive data: If your vacuum cleaner uses SLAM (Simultaneous Localization and Mapping, a technology that allows robots to build 3D maps and navigate indoor spaces) and uploads maps to the cloud, switch to local or offline mapping. Choose models that make this option clear and user-controlled.
- For connected cars: Do not link your vehicle account to your work email or phone number. Keep app permissions minimal, and if you operate near sensitive facilities, avoid parking connected cars within close range.
Conclusion: Ownership or Perpetual Surveillance Lease
In the connected-device economy, if the right to close the data pipe means the device stops functioning, you are not an owner but a renter paying an invisible fee in privacy, professional security, and even national safety. From robotic vacuums with active backdoors to fleets of electric cars, the shared lesson is unmistakable: intelligence without transparency and accountability is simply another name for surveillance.
If we want to live smart rather than live monitored, we must rewrite the rules of engagement in favor of the user and data sovereignty. That means transparent contracts, independent audits, secure network architectures, and the guaranteed right to a genuine local mode. Until these safeguards are verifiably present in the Chinese supply chain, common sense dictates maintaining operational distance from that ecosystem, particularly in a journalist’s home, a sensitive office, or behind the wheel of a car that could at any moment become a moving sensor.
